During my study at Temple University, I am strongly involved in research on multiple projects funded by the National Science Foundation (NSF), Army Research Organization (ARO), and Office of Naval Research (ONR). I am currently researching at the Center for Networked Computing (CNC) focusing on network technology and its applications. My research areas include Wireless Networks, Wireless Sensor Networks, Network Security, Network Forensics, and Cognitive Radio Networks. During this period, I have published twelve of my research results that include seven conference papers (IEEE ICPADS 2018, IEEE GLOBECOM 2019, IEEE ICC 2019, IEEE Sarnoff 2019, Resilience Week 2019), four journals (IJSN, IEEE TDSE, CPS, ISJN ), and a book chapter (Springer).
Involved Research Projects
- SpecEES: Collaborative Research: Study of the Tradeoff between Spectrum Allocation Efficiency and Operation Privacy in Dynamic Spectrum Access Systems (by National Science Foundation)
- NeTS: Coexistence of Heterogeneous Wireless Access Technologies in the 5 GHz Bands (by National Science Foundation).
- Moving Target Defense in Military Organization with Connected Dominating Set as Command Units (by Army Research Office).
- Cyber Forensics Toolkit for Machinery Control (by Office of Naval Research).
Source Location Privacy
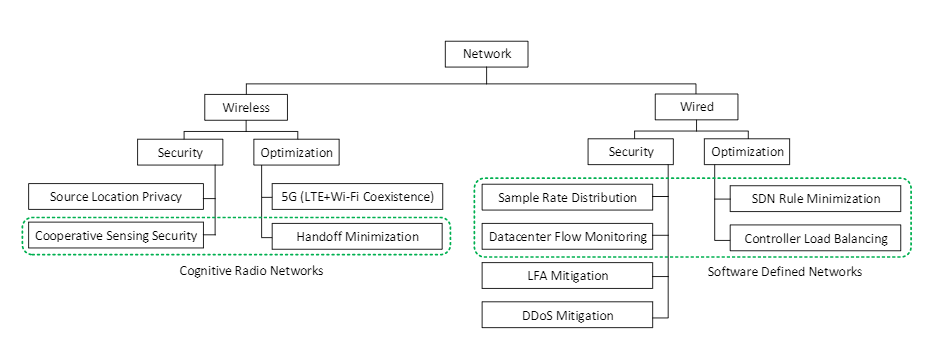
I have conducted research on source location privacy which is an important security issue in wireless sensor networks. Military operations on a battlefield without a communication infrastructure is viewed as a wireless sensor network. Our proposed controlled routing protocol can hide the location of the commander by compromising the performance a little. We propose the controlled routing protocol, a mixture of shortest path and random routing protocols that maintain a good balance between security and efficiency. Our proposed protocol is based on two principles: if all the messages do not follow the same path, then backtracking to the source node is not possible and when an adversary is very far away from the source and destination locations, then efficiency is more important than security. Nodes in our proposed routing protocol forward the messages either to the node on the shortest path or a random neighbor with a variable probability. The probability of taking the shortest path increases by distance from the source and the destination node. This research is a part of the project In Moving Target Defense in Military Organization with Connected Dominating Set as Command Units which is funded by ARO [4].
Cognitive Radio Network Technologies
I have also researched in the area of cognitive radio network technologies and wireless spectrum sharing. In cooperative spectrum sensing in a cognitive radio network, a secondary user decides about the presence of the primary user based on its own and other secondary users’ sensing results. An error in determining the correct primary user presence leads a secondary user to transmit and cause interference with the primary user, which is unexpected. Some malicious secondary users send incorrect sensing information to others to change their sensing results. We proposed a reputation-based mechanism to mitigate this kind of attack [2,10]. We have also worked on minimizing the number of channel switches of cognitive radio users. In cognitive radio ad-hoc networks the mobile users form a distributed multi-hop network using the unused spectrum. The qualities of the channels are different in different locations. When a user moves from one place to another, it needs to switch the channel to maintain the quality-of-service required by different applications. We study the mobility patterns of users, predict their next locations, and probabilities to move there based on its history. Then, we extract the mobility patterns from each user’s location history and match the recent trajectory with the patterns to find future locations. We construct a spectrum database using Wi-Fi access point location data and the free space path loss formula. We propose a machine learning-based mechanism to predict the spectrum status of some missing locations in the spectrum database. We proposed a method to select the current operating channel to minimize the total number of channel switches during the next moves of a user [3].
In another work, we proposed a mechanism to ensure fair coexistence of LTE and Wi-Fi in 5GHz bands. The declaration stating that 5GHz bands are unlicensed enables LTE to operate on 5GHz bands. In existing LTE-U systems, the LTE base station (eNB) estimates a fair portion of Wi-Fi usage based on channel state information which is not accurate for many reasons. In our proposed system, Wi-Fi access points share their usage information via wired medium with LTE eNBs. LTE eNBs adjust the LTE duty cycle to ensure fairness between LTE and Wi-Fi users. The model performs better than existing models in the area where the operator has both LTE and WiFi network coverage. The experiments were done in two indoor scenarios [11]. These researches are parts of two projects, SpecEES: Collaborative Research: Study of the Tradeoff between Spectrum Allocation Efficiency and Operation Privacy in Dynamic Spectrum Access Systems and NeTS: Coexistence of Heterogeneous Wireless Access Technologies in the 5 GHz Bands that are funded by NSF.
Network Forensics
Detecting DoS attacks and identifying attackers have been an important issue in Network Forensics. Moreover, DoS attacks are increasing day by day in both number and size. We proposed a DDoS mitigation mechanism using a special type of router called a filter router. The victim can protect itself and reduce useless congestion in the network by sending filters to filter routers for blocking attack traffic. The victim needs to select a subset of filter routers wisely to minimize attack traffic and blockage of legitimate users. We formulate two problems for finding filter assignment with a budget (limited number of filters) and provide greedy and dynamic programming solutions. We considered the system will block all the DDoS traffic before reaching the victim. The system becomes more practical by allowing some attack traffic that does not exceed the bandwidth limit of the victim. The victim’s operation is not hampered if the total incoming traffic does not exceed its capacity. We formulate a problem for selecting filter routers given a budget on the number of filters. The problem considers that the victim has limited incoming bandwidth and we provide an optimal dynamic programming solution. We also use filters and filter routers to defend against the transit-link DDoS attack. A transit-link DDoS attack is a special attack in which the attacker sends out a huge number of requests to exhaust the capacity of a link on the path the traffic comes to a server. The filters used here are slightly different; a filter from servers can block a link incident to a filter router. By analyzing traffic rates and paths, the victim can identify some links that may be congested. The victim selects some of these possible congested links and sends filters to the corresponding filter routers so that the legitimate traffic follows non-congested paths. We formulate an optimization problem for selecting the minimum number of possible congested links so that the legitimate traffic goes through a non-congested path. We transform the problem to the vertex separation problem to find the links to block. In another research, we study the distribution of sample rates for detecting DDoS attacks in software-defined networking datacenters. Usually, in a data center, virtual machines are used as monitors to monitor all the flows. In such a system, virtual machines run a machine learning method to detect DDoS behavior but it can only process a limited number/amount of flows. When the amount of flows is beyond the capacities of all monitor virtual machines, the system sub-samples each flow probabilistically. The sampling rate affects the DDoS detection rate of the monitors. We investigate the relationship between the sampling rate and the DDoS detection rate. Then, we formulate an optimization problem for finding an optimal sampling rate distribution and solve it using mix-integer linear programming. We conduct extensive experiments with Hadoop and Spark in our datacenter at Temple University to support the feasibility of our model. These researches are partially funded by multiple NSF and REU Site grants [1, 5, 6, 7, 8].
Cyber Forensics Toolkit for Machinery Control
I have worked on the project Cyber Forensics Toolkit for Machinery Control which was funded by ONR. This project required to develop a toolkit to find the security issues in the small devices which are used in navy ships to control large machinery. While working on this project I have analyzed and discovered many security issues in many microcontrollers and PLCs including, Arduino, Freescale Device, Amel SAMAD2, Allen Bradly PLC, and other devices. Using each device we tried to develop malicious programs and find the effects of the programs on the CPU, memory, and performances. Analyzing the behavior of the device we develop a tool to detect malicious behavior of the device. We also worked with berkeley packet filter (BPF) to filter out the attack traffic at some of the PLCs. Despite being this project in partnership with a company called TDI Technologies, I had real research experience with the real devices that are used in large ships of US NAVY. This project helped me to work with sophisticated and highly secured devices that is rare in academic institutions.
1. R. Biswas and J. Wu, “Optimal Filter Assignment Policy Against Distributed Denial-of-Service Attack,” in IEEE Transactions on Dependable and Secure Computing in 2020.
2. R. Biswas, J. Wu, X. Du and Y. Yang “Mitigation of the spectrum sensing data falsifying attack in cognitive radio networks”, in Cyber-Physical Systems, in 2020.
3. R. Biswas and J. Wu, “Minimizing the Number of Channel Switches of Mobile Users in Cognitive Radio Ad-Hoc Networks” in J. Sens. Actuator Netw. 2020, 9, 23.
4. R. Biswas, and J. Wu. “Preserving source and destination location privacy with controlled routing protocol.” International Journal of Security and Networks 13.3 (2018)
5. R. Biswas, J. Wu, and Y. Chen,” Optimal Monitor Placement Policy Against Distributed Denial-of-Service Attack in Datacenter, ” Resilience Week 2019 Symposium, November 4-7, 2019.
6. R. Biswas, J. Wu, and A. Srinivasan,” Cost-Aware Optimal Filter Assignment Policy Against Distributed Denial-of-Service Attack, ” Resilience Week 2019 Symposium, November 4-7, 2019.
7. R. Biswas, J. Wu, and X. Li ” A Capacity-Aware Distributed DoS Attack in Low-Power and Lossy Networks” The 40th IEEE Sarnoff Symposium 2019.
8. R. Biswas, J. Wu, W. Chang, and P. Ostovari ” Optimal Filter Assignment Policy Against Transit-link Distributed Denial-of-Service Attack” IEEE Global Communications Conference (2019)
9. R. Biswas, and J. Wu. ” Filter Assignment Policy Against Distributed Denial-of-Service Attack.” The 24th International Conference on Parallel and Distributed Systems (2018)
10. R. Biswas, J. Wu., and X. du “Mitigation of the Spectrum Sensing Data Falsifying Attack in Cognitive Radio Networks” IEEE International Conference on Communications (2019)
11. R. Biswas, and J. Wu. ” Co-existence of LTE-U and Wi-Fi with Direct Communication.” IEEE International Conference on Communications (2019)
12. R. Biswas, and J. Wu. “Cognitive Radio Network Technologies and Applications.” Emerging Wireless Communication and Network Technologies. Springer, Singapore, 2018. 13-36.